Introduction
The OSI standard has led to efficient protocol design because of the strict and clear boundaries between the layers. Each layer makes no assumptions about the adjacent layers, other than that they will be capable of pre-defined interactions as specified by the OSI standard that means lower layers provides services to the above layer. Thus, a single layer can be upgraded or replaced without affecting the design of the other layers.
Over the last three decades, this approach has been shown to produce modular, robust and enduring communication system. In [2], the authors present historical examples of well-defined architecture which have led to long-term success for a number of different designs.
Wireless communications and networking occupy center stage in research and development activity in the area of communication networks. Recent research has shown that the OSI model is not necessarily the correct approach for some modalities of wireless communication. Researchers have made some modification to communication protocols which violets the OSI model, but achieves specific optimization goals. These modifications are termed as “cross layer design (CLD)” [1].Thus, there are number of cross-layer design proposals in the literature. The main motivation for cross layer design is human mentality and psychology. If a new design paradigm is proposed, we compare it with the existing one. Hence the concept of cross layer design must be compared with the traditional layered architecture so that people can be motivated towards the use of the violation of the layered design.
Cross layer design is described in different ways. They are:
“Cross-layer design refers to protocol design done by actively exploiting the dependence between protocol layers to obtain performance gains”, “Violation of a layered architecture is cross-layer design with respect to the reference architecture”, “The core idea is to maintain the functionalities associated to the original layers but to allow coordination, interaction and joint optimization of protocols crossing different layers”, “Cross-layer design is defined as a protocol design methodology. However, a protocol design with this methodology is also termed as a cross-layer design”
Cross Layer Design Proposals
While reviewing various works by the researchers, we came across a large number of Cross-Layer Design Proposals based on the published research articles. Many of the cross-layer designs proposals require creation of new interfaces between the layers preferably non-adjacent layers. These can further be divided into three categories depending onthe direction of information flow along with the new interfaces:
Upward Information Flow
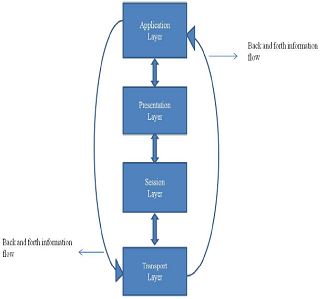
It is a scheme which proposes the idea of having direct access between two layers where the flow of the information comes from the lower layer to the higher layer. This scheme proposes that one higher layer is exposed to the lower layer requests which are forbidden by the architecture.
The formation of another interface from the lower layer to the higher layer at runtime is an outcome, when higher-layer requires data from the lower-layer(s), as appeared in figure 1. Making interfaces from the lower layers to the higher layer to empower unequivocal notices. Upward data stream fills the need of informing the higher layers about the hidden network conditions.
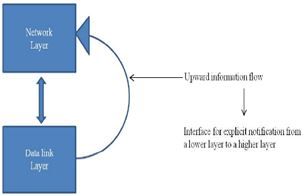
Figure 1: upward movement of data
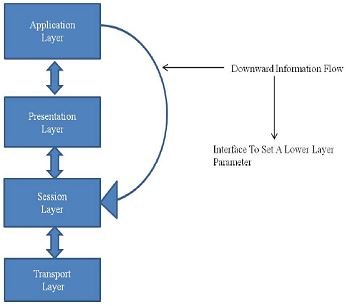
Downward Information Flow
Some Cross layer design recommendations depend on setting parameters on lower layer of stack at runtime utilizing an immediate interface from some higher layer, as delineated in figure 2. A decent approach to take a gander at upward and downward information flow is to regard them as warnings and insights individually. Downward information flow is intended to give indications to lower layers about how application information ought to be handled.


 ©
©